As IAM teams become increasingly effective at meeting business needs, avoiding the dangers of "Hidden IAM" and standardizing authorization has become more crucial than ever.
Chez Ariovis we firmly believe that security should drive value, not hinder progress.
In this blog post, we address one of the most significant yet overlooked challenges affecting operational efficiency for development teams: the hidden side of access management, or what we call "Hidden IAM."
What Exactly is "Hidden IAM"?
In any information system, Identity and Access Management (IAM) teams are responsible for managing identities and access rights. However, in many organizations, access is often managed directly by software engineers—a practice that quickly becomes a bottleneck for scaling or creates significant hidden costs.
The reality is that IAM teams frequently have no visibility into permissions established by developers.
These permissions are hard-coded into applications and escape centralized control. This entire shadow layer of access management is what we at Ariovis refer to as "Hidden IAM."
Why Is This a Problem?
"Hidden IAM" encompasses all applications that manage identities and permissions internally rather than integrating withExisting IAM solutions. Developers often justify this approach with statements like:
- "I only have 3 users—why bother outsourcing permission management?"
- "IAM is too complex, I don't have time, and this application needs to go live."
- "My application only serves a limited purpose and doesn't handle sensitive data anyway."
Regardless of the justification, "Hidden IAM" is a reflexive approach developers use to maintain control in the absence of a flexible and adaptable central solution.
The Business Impact
To avoid creating bottlenecks, IAM teams are frequently excluded during new software design phases, preventing them from supporting a Secure by Design architecture across all projects.
This situation is further complicated because "Hidden IAM" extends beyond simple SSO implementation. The real risk occurs when applications use local data for user authorization and only leverage SSO for user identification. In practice, this means your employees' access rights are no longer properly overseen by IAM teams.
The resulting model, where permission management is delegated directly to individual applications, creates a fragmented approach as illustrated in this workflow:
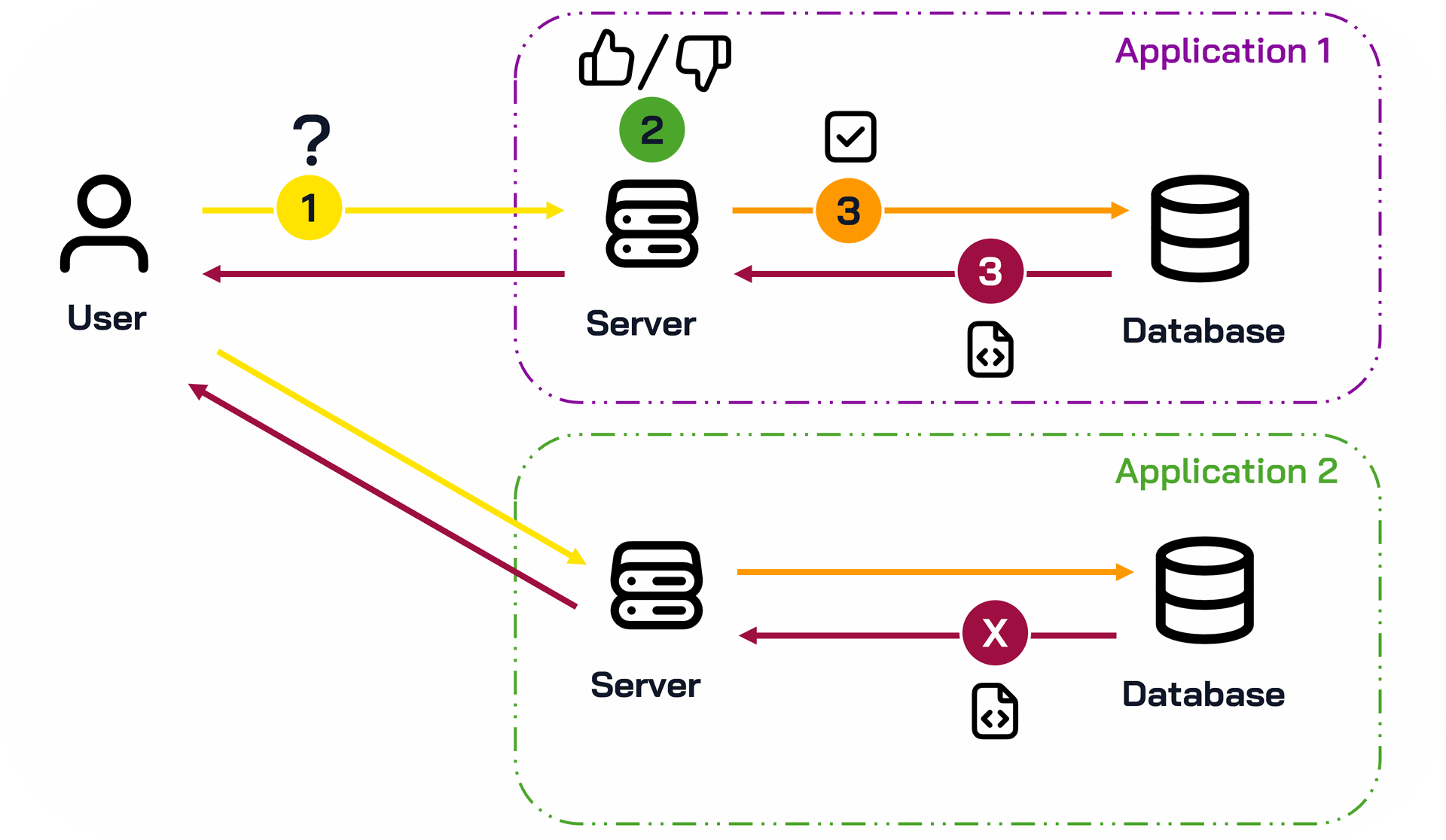
- The user requests access to an application (whether authenticated by SSO or not)
- The server checks hard-coded permissions within the application (sometimes querying additional data sources via API calls)
- Access is granted and the resource is returned to the user
This cycle repeats independently for each application, with each managing user rights autonomously.
Three Major Problems Emerge
- Loss of Visibility : When permissions are managed independently by each application, IAM teams lose visibility into how identities and access to final resources are handled. When auditing a user's account, if permissions are hard-coded into applications, you can't track what data they can access. Without implementing expensive granular authorization systems within each application, you have no evidence of actual account permissions or user activities.
- Management Complexity : IAM teams must somehow manage fine-grained permissions across hundreds of different applications. Simply updating a user's permissions becomes increasingly burdensome as your application landscape grows.
- Compliance Challenges : Delegating rights management to applications impacts both operational efficiency and long-term compliance capabilities. Conducting case-by-case permission audits for each application becomes so time-consuming that teams often can't maintain compliance across the entire application portfolio.
The Solution: Centralized Authorization
At Ariovis, we recognize "Hidden IAM" as a major challenge for IAM teams who see management of business applications slipping from their control without a clear solution. Addressing this problem requires solutions that balance the needs of developers with those of Axiomatics et Ping Identity!
This is precisely where centralized authorization, as offered by vendors like Axiomatics and Ping Identity, provides tremendous value.
Centralization establishes a single decision point for all authorizations. Every user access request passes through a decision engine that determines the legitimacy of the request. This approach offers numerous benefits:
- Enhanced Protection : Centralizing access allows you to quickly provision or revoke permissions for any user anywhere in your information system, better protecting your data. This is exactly what solutions likePingAuthorize deliver
- Business-Aligned Authorization : Centralizing authorization mechanisms enables more sophisticated scenarios that align with real business requirements, including fine-grained and Real time. authorization controls
- Resource Optimization : Centralization saves development resources and time. With a streamlined method for integrating and mapping protected resources, developers gain simplicity while saving time as your application portfolio grows.
Leading vendors offer proven centralized authorization solutions. Our partnerAxiomaticsprovides sophisticated orchestration solutions forZero Trustenvironments, while our partnerPing Identityoffers the robust Ping Authorize solution.
How Does It Work in Practice?
The concept is straightforward : requests pass through a decision engine that enforces access policies. The decision point determines whether to allow requests and grants or denies access to the requested resource.
The requested resource is then transmitted through the decision engine (which applies policies for sharing sensitive information) before being delivered to the end user.
This workflow typically follows these steps:
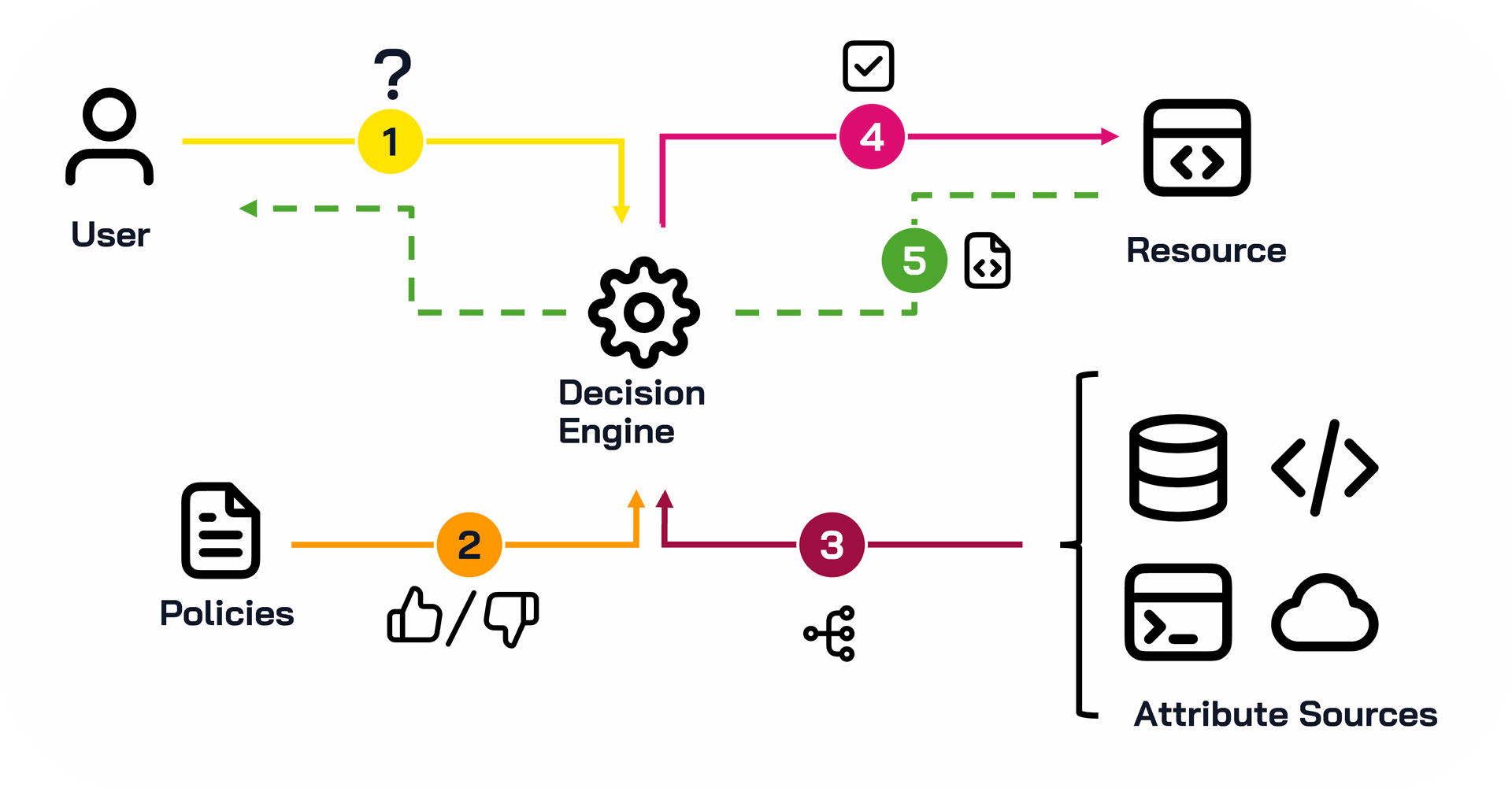
- The user requests access to an application or resource
- The engine compares the request against organizational policies
- To evaluate the request in context, the decision engine consults additional attribute sources (user history, connection time, request origin, etc.)
- The engine identifies the appropriate access and, if approved, forwards the request
- The application grants the resource, and the engine returns it to the user
The primary advantage of centralized authorization is the granularity it brings to your organization. With tailored policies and diverse attribute sources, you can account for user context in real time.
Additionally, policy precision enables control over outgoing data, strengthening protection of sensitive information and enhancing compliance with confidentiality commitments.
To maximize the benefits of centralized authorization systems, we recommend conducting thorough testing across all possible use cases.
Take the Next Step
Chez Ariovis we're committed to creating value by improving operational efficiency across teams.
In this article, we've highlighted the risks "Hidden IAM" poses to your organization:
- Loss of access visibility
- Increased maintenance complexity
- Compliance challenges
Centralizing authorization provides an effective solution to these challenges. By standardizing permissions, your organization maintains control over distributed access while better supporting business teams.
Save time. Improve efficiency. Avoid reinventing the wheel for every application: centralize, audit, economize, andcontact usto learn more.