Bridging the Gap Between Security and Business Needs
In 2025, organizations continue to struggle with authorization management. Technical complexity and miscommunication between IT and business teams often create bottlenecks that slow down enterprise agility.
While access policies have always been fundamental to applications, today's landscape is dramatically different. Generative AI is transforming this space by bridging the divide between business requirements and technical implementation.
Generative AI: Transforming IAM Teams
In 2025, generative AI has opened new possibilities across multiple industries. For IAM teams specifically, it serves as a powerful force multiplier that extends their capabilities and unlocks strategic opportunities.
IAM professionals can now escape the endless cycle of technical translations and implementations. Instead, they're free to focus on what truly matters: crafting innovative security strategies, enhancing identity governance, and aligning security with business goals.
This shift creates a compelling opportunity for organizations to turn access management from a necessary burden into a strategic business advantage.
From Business Language to Secure Code: Finally Bridging the Gap
After more than a year of deploying AI solutions for authorization, we've identified their main strength: they create bridges between business needs expressed in common language and tailored technical implementation.
This advancement solves one of the historical challenges of cybersecurity: communication between different stakeholders. On one side, business teams express functional needs; on the other, IAM experts translate them into operational policies.
This augmented collaboration enhances IAM expertise in its strategic dimensions:
- Designing access policies aligned with the overall security strategy
- Compliance with regulatory and contractual requirements
- Optimizing performance and security implementations
- Unified governance of access policies
AI and Access Control: A Human-Machine Synergy
To understand the value of this combined approach, let's take a concrete example:
Imagine that within a career management application, access rights must be adapted according to roles and hierarchical relationships. A manager should be able to supervise the objectives of their direct reports, while each employee should have limited rights to their own data.
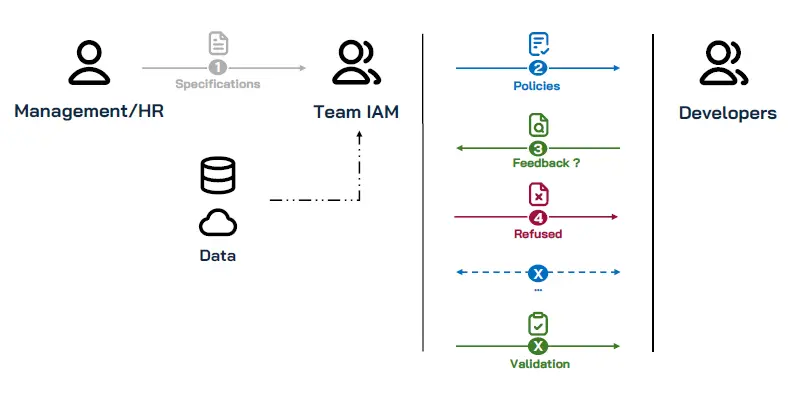
Without AI, this request would require:
- Detailed interpretation by IAM teams
- Numerous and complex technical data sources
- Implementation by developers
- Validation testing
- Successive adjustments in case of misunderstanding
With AI tools assisted by IAM experts, this same rule is first automatically translated into a technical access policy, then verified and refined by specialists before deployment. AI accelerates the process and reduces the number of back-and-forth exchanges between teams, but human expertise ensures its relevance and security.
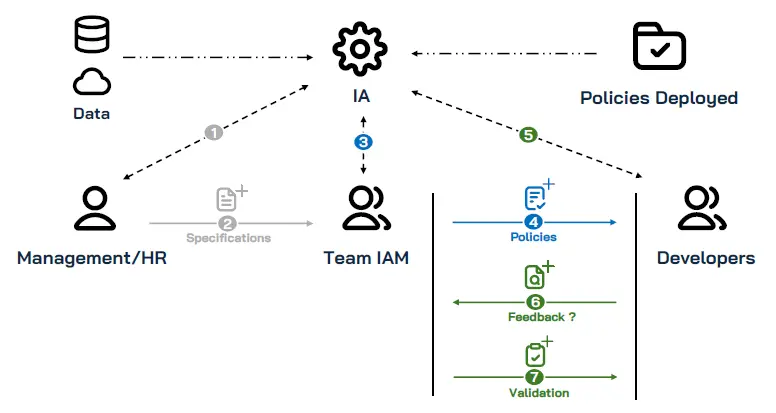
Implementing access policies with AI
Tangible Benefits of This Human-Machine Collaboration
Since we began supporting our clients through this transformation, we've observed tangible benefits for both IAM and business teams:
- Enhancing IAM expertise: specialists can focus on high-value tasks rather than repetitive technical translations
- Facilitated communication: reducing misunderstandings between business and technical teams
- Improved policy quality: rules are more precise and better aligned with actual needs, while remaining secure
- Enhanced documentation: security choices are naturally documented, facilitating audits and controls
- Increased adaptability: policy modifications can be proposed, validated, and implemented more quickly
But the most important benefit is undoubtedly the reconciliation between security imperatives and business needs. AI, under the supervision of IAM experts, allows security to become a facilitator rather than a constraint, ultimately improving operational efficiency.
Policy Companion: A Workflow Redesigned in 5 Steps
The market now offers several solutions that integrate generative AI to assist in access policy management. Players like Axiomatics with Policy Companion have adopted these technologies to complement—not replace—human expertise.
At Ariovis, we've developed a balanced approach to support our clients. We help them select and integrate these tools into their existing ecosystem and train their IAM teams to leverage these technologies effectively without losing control.
How does this synergy work in practice?
- Needs expression phase: Business teams formulate their access requirements in natural language
- Initial AI translation: The tool generates a technical version of these policies
- Validation and optimization by IAM experts: Specialists verify, correct, and optimize the generated policies
- Feedback to business for confirmation: AI translates the technical version back into accessible language
- Secure deployment: After final validation, IAM experts deploy the policies in the environment
Addressing the "Hidden IAM" Challenge
This collaborative approach also addresses the growing problem of "Hidden IAM" that we explored in a previous article When authorizations are hard-coded into applications, they escape centralized governance.
Using AI under the supervision of IAM experts enables:
- Easier standardization of access policies across the organization
- Facilitated adoption of centralized authorization solutions
- Limited development of fragmented authorizations that are difficult to audit
Our Vision for the Future
At Ariovis, we're convinced that generative AI, properly framed by IAM experts, will continue to positively transform identity and access management in the years to come. Our "Security Meets Business" approach finds an ideal balance in this human-machine collaboration.
We're transforming how business and security teams interact. Cybersecurity is no longer just a technical hurdle that few understand—it's becoming a business enabler that everyone can appreciate. While remaining firmly grounded in expert oversight, security becomes more accessible and valuable across all organizational levels.
Want to Learn More?
Find out how to integrate generative AI into your access management strategy with expert guidance from our IAM team, and stay ahead of the curve.Connect with us on LinkedIn to follow all of our activities and do not hesitate. to visit our web site !